¿Cómo escondo mi dirección IP?
¿Por qué necesito ocultar la dirección IP?
¿Qué es una dirección IP?
Una cadena de números que el proveedor de internet asigna automáticamente cuando usamos internet. Identifica el dispositivo en la red. A través del número, se puede saber dónde está navegando en la red. Esta es la dirección IP.
Una dirección IP es una cadena de números y puntos decimales que identifica cada dispositivo conectado a internet. La dirección IP es única para todos.
Usted proporciona su dirección IP real al sitio web cada vez que lo visita. Además, la dirección IP permite inferir fácilmente y con precisión la ubicación específica de un usuario. Incluso si simplemente navega y no hace nada, revelará su ubicación.
Para monetizar su comportamiento en línea, los sitios web y los anunciantes de terceros pueden utilizar estos big data para enviarle contenido específico, adivinar lo que le gusta, y luego enviarle más contenido y guiarlo a una compra.
¿Para qué se utilizan las direcciones IP?
Hoy en día, los recursos de información se desarrollan muy rápidamente, una variedad de productos científicos y tecnológicos, la tecnología también está mejorando cada vez más. Los diversos entornos que nos rodean están cambiando constantemente. Sin embargo, detrás de estos cambios, también hay muchos peligros que acechan. Muchas veces, debido a la información demasiado desarrollada y desbordada, es fácil tener situaciones de fuga de información. Durante el uso de productos de internet, su propia información personal se revela a medida que se expone la dirección IP. Incluso es posible ser adquirido o incluso explotado por otros sin que uno se dé cuenta.
¿Sabes para qué se utiliza tu dirección IP? La filtración de la dirección IP es teóricamente de poca importancia, pero se puede obtener de varias maneras para obtener más información sobre usted y así poder atacarlo.
- Obtenga su localización
La dirección IP puede ser usada para averiguar dónde está usando la red, y los rastreadores pueden usar esta información para reducir aún más su ubicación.
- Restricciones según IP
Conocer su dirección IP le permite hacer restricciones por IP, como restringir el acceso o el uso de su plataforma web, etc.
- Ataques de phishing
Puede recopilar información sobre sus mensajes de foro y otros mensajes basados en la IP para obtener su información de contacto y, en teoría, enviarle algunos correos electrónicos de phishing.
- Seguimiento de su actividad
Cuando utiliza algunas redes públicas, es posible monitorear su actividad en línea. Esto se puede hacer a través de una dirección IP.
- Ataques de denegación de servicio distribuido (DDoS)
Si un atacante conoce su IP, puede lanzar un ataque DDoS en su dispositivo. Lo hacen generando una gran cantidad de solicitudes de datos que parecen ser de su dirección IP para inundar su dispositivo y deshabilitarlo. Esto se llama IP spoofing.
La dirección IP filtrada tendrá estos riesgos. Puede ocultar la IP real local a través de IP proxy para proteger la seguridad de la privacidad personal y mejorar la garantía del uso de la red. También es una herramienta de cambio de IP que muchas personas eligen. Hay muchas maneras de proxy IP, muchas personas están usando nezha IP proxy, con múltiples líneas y velocidad rápida, no solo puede proteger la privacidad, sino también romper el problema de restricción de IP de la plataforma.
¿Cómo ocultar mi dirección IP?
¿Cómo ocultar mi dirección IP? ¿Conoces una buena manera de ocultar tu dirección IP?
La gente presta especial atención a su privacidad, especialmente cuando estamos en línea, no queremos que otros descubran nuestra dirección. En este momento, solo necesitamos instalar un software de cambio de ip en la computadora, para cambiar nuestra dirección a otra dirección, y la otra parte no lo descubrirá en absoluto.
Usar una VPN
VPN significa red privada virtual y es un servicio de software. En pocas palabras, se trata de cifrar todos los datos a través de un servidor VPN y luego conectarse a internet del país con la dirección IP virtual asociada al país que está asignando. Oculta tu ubicación real.
Trabajar con un servidor proxy
Proxy ip, la forma más recomendada de ocultar su ip.
1) ¿Qué es una IP proxy?
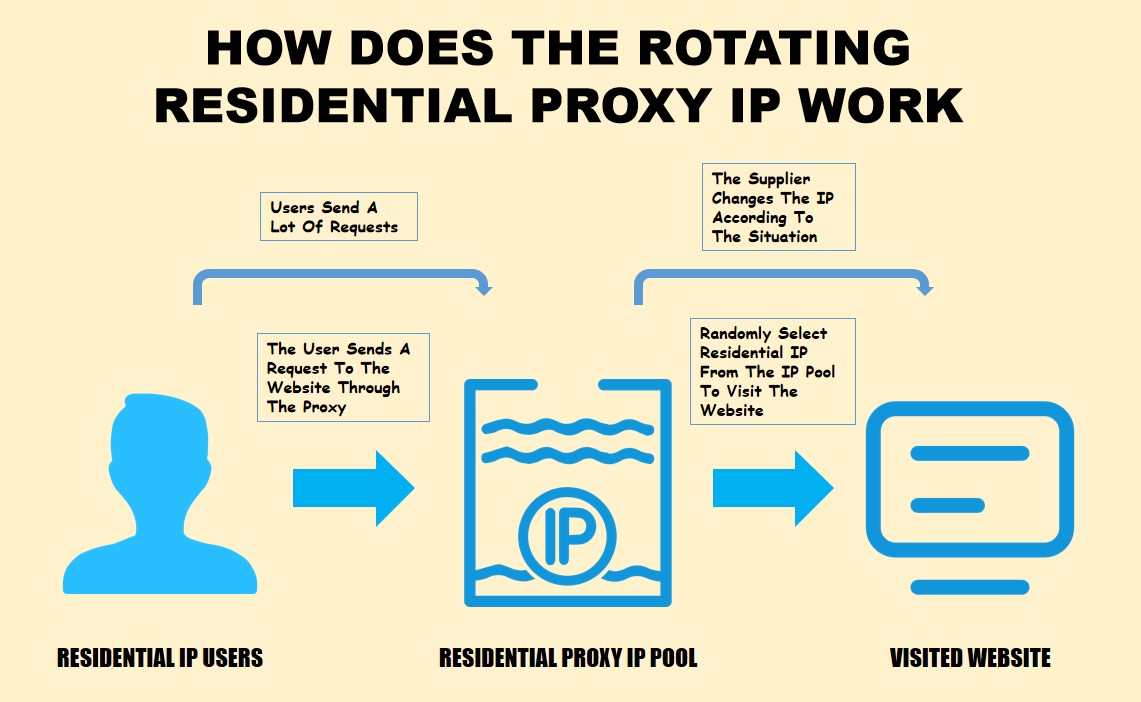
Las ip proxy son una forma popular de establecer conexiones de internet más seguras y privadas, así como de eludir cualquier restricción geográfica. ¿Cómo funciona proxy ip? En pocas palabras, se encuentra entre usted y el destino, permitiendo que el servidor intermedio enrute el tráfico al destino, con su IP real camuflada en el proceso y pasando de los servidores del proveedor de IP proxy a su nueva identidad.
Obviamente, ip proxy es más recomendado debido a su mayor privacidad, seguridad y estabilidad debido al cifrado de datos y una base de servidor madura en comparación con las siguientes herramientas. Siempre que, por supuesto, esté utilizando una aplicación proxy ip de calidad.
Proxy ip es un confiable y está disponible para las principales plataformas, incluyendo Windows, macOS, Android, iOS y Linux. Con más de 3000 servidores configurados en ubicaciones, esta ip proxy le permite cambiar la ip a cualquier lugar fuera de su área urbana. Junto con mucho soporte de protocolo, cifrado ECC y políticas de registro, proxy ip puede ser su solución definitiva para proteger su privacidad digital.
La demanda determina el mercado, y cuanto mayor sea la demanda, mayor será el mercado. Proxy ip no es una excepción. Innumerables proveedores de proxy crecen como lluvia durante la noche, y la calidad de proxy ip también es desigual. La IP en la bolsa es una IP dinámica de alta calidad que merece la pena recomendar. Antes de elegir una IP proxy, personalmente se recomienda probar más para comparar. También se llama comprar alrededor.
2) cómo proxy ip mantiene su privacidad segura
- Uso del protocolo proxy ip
Proxy ip con protocolo proxy ip. Diferentes protocolos ofrecen diferentes niveles de encriptación y velocidad de conexión. La mayoría de las ip proxy utilizan varios protocolos. En general, la seguridad del protocolo es inversamente proporcional a la velocidad de conexión. Cuanto mayor sea el nivel de cifrado, mayor será la latencia.
- Evita fugas de DNS
¿Qué es DNS? DNS significa sistema de nombres de dominio. En resumen, el DNS es como un directorio telefónico. Basado en DNS, las personas pueden rastrear la dirección IP de su proveedor de servicios de Internet (ISP). Si el DNS se rompe, su privacidad en línea corre el riesgo de ser expuesta al público. Una ip proxy con un sistema DNS encriptado puede ayudarlo a evitar fugas de DNS.
- Proteja su dirección IP
Una dirección IP es el mundo de internet, su número de identificación. La importancia de encriptar su dirección IP es obvia. Por lo general, los proveedores de servicios proxy ip implementan muchos servidores en todo el mundo. Cuando se conecta a una red a través de una ip proxy, su ISP y otros programas de terceros no pueden rastrear su verdadera dirección ip de fuerza, sino la dirección ip del servidor al que se conecta.
Es decir, una ip proxy te ayuda a ocultar tu dirección ip privada local. Entonces puede navegar por internet de forma anónima.
- Registro encriptado
La verdad es que nadie ofrece una política de ip proxy 100% cero registros. Incluso las ips proxy más confiables registran un pequeño número de registros, incluyendo información de usuario y registros de conexión. Los registros de actividad no están incluidos. Sin embargo, las ips proxy gratuitas generalmente registran registros de actividad, por lo que tenga cuidado al usar ips proxy gratuitas. La información del usuario, que contiene el nombre de usuario, la dirección de correo electrónico y la información de pago, se registra para la creación de cuentas de ip proxy y el pago de facturas. Los registros de conexión registran las conexiones entrantes y salientes de la ip proxy, así como las horas de inicio y final de la conexión. Por lo general, proxy ip recopila estos datos para mantener su soporte técnico.
La mejor solución para ocultar direcciones IP – ClonBrowser
¿Desea maximizar su privacidad y la seguridad de su dirección IP?
Se ha mencionado anteriormente que un proxy de prueba es un buen plan para proteger su dirección IP. ¡ClonBrowser es un excelente compañero cuando desea usar un proxy para ocultar su verdadera dirección IP!
Esto se debe a que ClonBrowser tiene una poderosa integración de proxy que sorprende. Proxies Luminati, Oxylabs proxies, HTTP Proxy y más para ofrecerle la mejor experiencia Proxy.
¿Eso es suficiente? ¡En realidad ClonBrowser es mejor de lo que piensas!
En primer lugar, satisface todas sus necesidades de cuentas múltiples, capaz de permitirle crear un sinnúmero de perfiles y lograr la gestión de cuentas múltiples. En segundo lugar, le permite trabajar de manera eficiente con su equipo. ClonBrowser siempre ha valorado mucho su trabajo en equipo.
¡ClonBrowser también tiene una poderosa función de protección de huellas dactilares y un equipo de servicio post-venta profesional! ¡Puedes confiar en él!